The Key Differences Unveiled: An In-Depth Analysis of IT and OT Cybersecurity
A - Introduction
 |
| IT vs OT Cybersecurity |
B - Understanding the importance of IT and OT cybersecurity
1- Protection of Sensitive Data:
2- Operational Continuity:
3- Interconnectivity:
4- Compliance and Regulatory Requirements:
5- Enhanced Resilience:
To conclude, understanding the importance of both IT and OT cybersecurity is crucial for organizations in today's digital landscape. Neglecting cybersecurity in either domain can result in severe consequences, including financial loss, reputational damage, operational disruptions, and potential physical harm.
By adopting a proactive and integrated approach to
cybersecurity, organizations can mitigate risks, protect sensitive data, ensure
operational continuity, and comply with regulatory requirements.
C - The key differences between IT and OT systems
IT (Information Technology) and OT (Operational Technology) are two distinct types of systems that play crucial roles in organizations.
While they both contribute to the smooth functioning of businesses, it is
essential to understand the key differences between them in terms of their
functions and security requirements.
1- Function and Purpose:
IT systems primarily focus on managing and processing
digital information within an organization. They include networks, servers,
computers, software applications, and databases that handle administrative
tasks, data storage, communication, and information processing. The goal of IT
systems is to support business operations, improve efficiency, and enable
decision-making.
2- Connectivity and Network:
IT systems are typically connected through corporate
networks, the internet, and cloud-based services. They rely on standardized
protocols and communication technologies to facilitate data exchange,
collaboration, and remote access. IT networks are designed to prioritize data
transfer speed, bandwidth, and scalability to support diverse applications and
user requirements.
3- Safety and Reliability:
IT systems primarily deal with virtual assets, such as data,
software, and digital services. While data integrity, confidentiality, and
availability are critical for IT security, the primary concern is to protect
information and prevent unauthorized access. IT systems generally have multiple
layers of security measures, including firewalls, encryption, access controls,
and regular software updates.
4- Lifecycle and Change Management:
IT systems typically have shorter lifecycles due to rapid
technological advancements and evolving business needs. Regular updates,
software patches, and system upgrades are common in IT environments to improve
functionality, address vulnerabilities, and adapt to changing requirements. IT
change management processes involve rigorous testing, documentation, and
deployment procedures to minimize disruptions and ensure system reliability.
In contrast, OT systems often have long lifecycles due to
their criticality, complexity, and high costs associated with upgrades or
replacements. Changes to OT systems require careful planning, rigorous testing,
and regulatory compliance to avoid disruptions to ongoing operations. OT change
management processes must consider the impact on safety, operational
continuity, and compliance with industry standards.
D - Analysis of common cybersecurity threats for IT systems
1- Malware Attacks:
2- Phishing and Social Engineering:
3- Password Attacks:
4- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks:
5- Insider Threats:
6- Advanced Persistent Threats (APTs):
7- Web Application Vulnerabilities:
IT vs OT Cybersecurity - DevSecOps
8- IoT
Security Risks:

As the number of Internet of Things (IoT) devices deployed in organizations increases, so does the risk of compromised IT systems. Insecure IoT devices, lacking proper authentication, encryption, or vulnerability management, can serve as entry points for cyber attacks.
Organizations should ensure robust IoT device security, including proper
network segmentation, regular firmware updates, and secure configurations.
By being aware of these common cybersecurity threats, organizations can proactively implement appropriate security controls, educate their workforce, and continuously monitor their IT systems to detect and respond to potential attacks.
It is crucial to adopt a comprehensive
cybersecurity strategy that aligns with industry best practices and standards
to safeguard IT systems from evolving threats.
E - Analysis of common cybersecurity threats for OT systems
1- Operational Technology Malware:
2- Supply Chain Attacks:
Supply chain attacks pose a significant threat to OT systems. Adversaries can compromise the hardware, software, or firmware during the manufacturing or distribution process, leading to the insertion of backdoors or malicious code into the OT devices.
These compromised devices can then be deployed within organizations, providing attackers with unauthorized access and control over critical infrastructure.
There are multiple solutions in the market currently to analyze and provide a list of sub-component of software, patches, upgrades and to identify the vulnerabilities within those sub-components. The asset owners can be assured that any OEM software is scanned thoroughly before being installed on their networks. This list is called Software Bill of Materials - SBOMs.
3- Insider Threats:
Insider threats in the context of OT systems refer to unauthorized or malicious actions by individuals within the organization who have access to sensitive operational technology. This could include disgruntled employees, contractors, or third-party vendors.
Insider threats can result in
physical damage, data theft, or disruption of critical processes. Implementing
strong access controls, monitoring user activities, and conducting background
checks can help mitigate the risks associated with insider threats.
4- Remote Access Attacks:
As remote access to OT systems becomes more common, organizations face an increased risk of remote access attacks. Unauthorized individuals or cybercriminals may attempt to exploit vulnerabilities in remote access solutions, such as virtual private networks (VPNs), remote desktop protocols (RDP), or web-based interfaces, to gain unauthorized access to OT networks, and this also can be implemented to pass through diodes or cross domain solutions.
Implementing secure remote access controls, multi-factor
authentication, and intrusion detection systems can help prevent remote access
attacks.
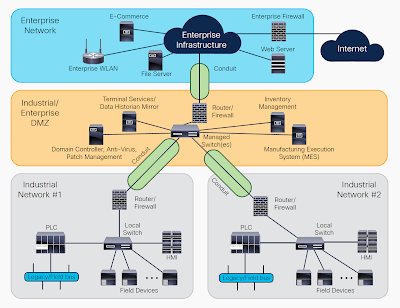
5- Lack of Network Segmentation:
OT systems are often intermingled with IT systems, leading to a lack of proper network segmentation. This lack of isolation can allow attackers to move laterally between IT and OT networks, increasing the potential for unauthorized access and control over critical operational technology.
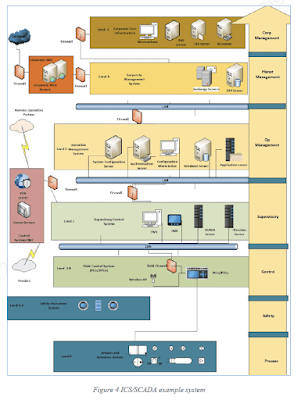
 |
| IT vs OT Cybersecurity - Segmenting the Network as per IEC 62443 |
Implementing network segmentation measures, such as firewalls,
virtual local area networks (VLANs), and access control lists, can help limit
the impact of a compromise in one network on the other.
6- Legacy Systems and Outdated Technology:
7- Physical Security Breaches:
Unlike IT systems, OT systems are often physically accessible, making them vulnerable to physical security breaches. Unauthorized access to the physical infrastructure, such as control rooms, substations, or industrial sites, can lead to tampering with critical equipment, theft of sensitive data, or disruption of operations.
Implementing physical security
measures, such as surveillance cameras, access control systems, and intrusion
detection systems, can help prevent physical security breaches.
By being aware of these common cybersecurity threats for OT systems, organizations can develop a comprehensive cybersecurity strategy that addresses the unique challenges and vulnerabilities of their operational technology infrastructure.
It is crucial to continually monitor, assess, and
enhance the security measures in place to protect critical infrastructure from
evolving threats.
F - Best practices for securing IT systems
Securing IT systems is vital for organizations to protect sensitive data, maintain operational efficiency, and mitigate the risks of cyber threats. Implementing best practices can help organizations establish robust security measures and strengthen their overall cybersecurity posture.
Here are some best practices for securing IT systems:
1- Regular Security Updates and Patch Management:
2- Strong Password Management:
3- Employee Training and Awareness:
4- Network Segmentation:
5- Endpoint Protection:
6- Regular Data Backups:
7- Incident Response Plan:
8- Continuous Monitoring and Threat Intelligence:
9- Regular Security Audits and Penetration Testing:
10- Vendor Risk Management:
By implementing these best practices, organizations can
strengthen the security of their IT systems and mitigate the risks associated
with cyber threats. It is essential to regularly review and update security
measures to stay ahead of evolving threats and protect critical data and
infrastructure.
F - Best practices for securing OT systems
Securing OT (Operational Technology) systems is equally important as securing IT systems.
Unlike IT systems that primarily deal with information, OT systems are responsible for the control and management of physical processes in industries such as manufacturing, energy, and transportation.
While the goals of securing OT systems align with IT systems, there are key differences and additional factors to consider.
Here are some
best practices for securing OT systems:
1- Segregation of Networks:
2- Implementing Network Monitoring:
3- Secure Remote Access:
4- Regular Patching and Updates:
5- Physical Security Measures:
6- Vendor Risk Management:
7- Incident Response and Business Continuity Planning:
8- Regular OT-specific Security Training:
9- Asset Inventory and Risk Assessment:
10- Regulatory Compliance:
By adopting these best practices, organizations can enhance
the security posture of their OT systems and protect critical operational
processes from potential threats. Just like with IT systems, it is crucial to
regularly review and update security measures to address evolving risks and
maintain a resilient OT infrastructure.
G - The need for a holistic cybersecurity approach
The ever-increasing threat landscape and the convergence of IT (Information Technology) and OT (Operational Technology) systems necessitate a holistic cybersecurity approach.
While implementing best practices for securing OT systems is crucial, it is essential to recognize that a comprehensive cybersecurity strategy encompasses both IT and OT domains.
Here's
why a holistic approach is necessary:
1- Understanding the Interdependencies:
2- Addressing Vulnerabilities Across the Spectrum:
3- Coordinating Incident Response:
4- Leveraging Synergies:
5- Compliance with Regulatory Requirements:
Regulatory frameworks often span both IT and OT domains, mandating the implementation of specific security controls and practices. Organizations must comply with these requirements to avoid penalties and maintain their legal and regulatory standing.
A holistic approach ensures that
all applicable regulations are met, reducing compliance risks.
To achieve a holistic cybersecurity approach, organizations
should consider the following:
Establishing a cybersecurity governance framework that considers the unique characteristics of both IT and OT domains.
- Conducting regular risk assessments to identify and prioritize vulnerabilities across the entire spectrum.
- Implementing comprehensive security controls, including network segmentation, access controls, encryption, and monitoring, for both IT and OT systems.
- Developing a robust incident response plan that addresses incidents holistically and involves stakeholders from both IT and OT domains.
- Providing regular cybersecurity training and awareness programs to employees across the organization, emphasizing the importance of a holistic approach.
- Collaborating with internal and external stakeholders, including IT and OT teams, vendors, industry forums, and regulatory bodies, to exchange knowledge and share best practices.
By embracing a holistic cybersecurity approach,
organizations can effectively mitigate the evolving cyber threats targeting
both IT and OT systems. It is vital to recognize that cybersecurity is a
collective responsibility and requires a collaborative effort from all
stakeholders to safeguard critical infrastructure and operations.
H - Conclusion: Emphasizing the criticality of IT and OT cybersecurity in today's interconnected world
To achieve a holistic cybersecurity approach, organizations
should establish a cybersecurity governance framework, conduct regular risk
assessments, implement comprehensive security controls, develop a robust
incident response plan, provide regular cybersecurity training and awareness
programs, and collaborate with internal and external stakeholders.